- Install Metasploit On Windows 10
- Download Metasploit Windows 10
- Download Metasploit 32 Bit Windows
- Metasploit Pro 32 Bit Download
- Get code examples like.
- Metasploit free download. WebSploit Framework WebSploit Advanced MITM Framework +Autopwn - Used From Metasploit For Scan and Exploit Target Se. 32-bit MS Windows.
- This is Metasploitable2 (Linux) Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools, and practice common penetration testing techniques.
- Metasploit Express for Linux 32 bit v.4.0.0 Advertisement Metasploit Express is security software for security professionals in enterprises and government agencies who need to carry out penetration tests against their systems quickly and easily.
The Metasploit Framework is a tool created by Massachusetts-based security company Rapid7 to help security professionals perform penetration testing tasks and discover security vulnerabilities and IDS signature development. The Metasploit Framework provides the infrastructure, content, and tools to perform extensive security auditing.
This is Metasploitable2 (Linux) Metasploitable is an intentionally vulnerable Linux virtual machine. This VM can be used to conduct security training, test security tools,. Download metasploit 32 bit windows 10 for free. Security tools downloads - Metasploit by Rapid7 LLC and many more programs are available for instant and free download.
Metasploit Pro is the full-featured edition of Metasploit, the world’s leading penetration testing solution, and is designed for enterprise security programs and advanced penetration tests. Metasploit allows you to test your defenses by safely simulating attacks on your network to uncover security issues. Metasploit can also be used to validate vulnerabilities as part of your vulnerability management program.
Metaploit Pro includes all features of Metasploit. Features that are exclusive to Metasploit Pro are:
- Conduct advanced penetration tests
- Validate vulnerabilities
- Audit your web applications
- Measure your exposure to phishing attacks
Take advantage of our free 14-day trial of Metasploit Pro today and start protecting your network with the world’s most used penetration testing solution.
Kali Linux is preinstalled with over 600 penetration-testing programs, including nmap (a port scanner), Wireshark (a packet analyzer), John the Ripper (a password cracker), Aircrack-ng (a software suite for penetration-testing wireless LANs), Burp suite and OWASP ZAP (both web application security scanners). Kali Linux can run natively when installed on a computer's hard disk, can be booted from a live CD or live USB, or it can run within a virtual machine. It is a supported platform of the Metasploit Project's Metasploit Framework, a tool for developing and executing security exploits.
It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of BackTrack, their previous forensics Linux distribution based on Ubuntu. The third core developer Raphaël Hertzog joined them as Debian expert.
Kali Linux is based on Debian Wheezy. Most packages Kali uses are imported from the Debian repositories.
Kali Linux is developed in a secure location with only a small number of trusted people that are allowed to commit packages, with each package being signed by the developer. Kali also has a custom built kernel tha is patched for injection. This was primarily added because the development team found they needed to do a lot of wireless assessments.
What's New:
We are incredibly excited to announce our fourth and final release of 2019, Kali Linux 2019.4, which is available immediately for download.
2019.4 includes some exciting new updates:
- A new default desktop environment, Xfce
- New GTK3 theme (for Gnome and Xfce)
- Introduction of “Kali Undercover” mode
- Kali Documentation has a new home and is now Git powered
- Public Packaging – getting your tools into Kali
- Kali NetHunter KeX – Full Kali desktop on Android
- BTRFS during setup
- Added PowerShell
- The kernel is upgraded to version 5.3.9
- … Plus the normal bugs fixes and updates.
New Desktop Environment and GTK3 Theme
There are a ton of updates to go over for this release, but the most in your face item that everyone is going to notice first are the changes to the desktop environment and theme. So let’s cover that first.
An update to the desktop environment has been a long time coming. We have been talking about how to address this, what we wanted to do, experimenting on different approaches, and so on for months now. As a summary we had a few issues we wanted to address head-on:
- Performance issues – Gnome is a fully-featured desktop environment with a ton of awesome things it can do. But all these features comes with overhead, often overhead that is not useful for a distribution like Kali. We wanted to speed things up, and have a desktop environment that does only what it’s needed for, and nothing else. Gnome has been overkill for most Kali users, as many just want a window manager that allows you to run multiple terminal windows at once, and a web browser.
- Fractured user experience – We support a range of hardware, from the very high end to the very low. Because of this, traditionally our lower-end ARM builds have had a completely different UI than our standard. That’s not optimal, and we wanted to unify this experience so it did not matter if you were running on a bare metal install on a high end laptop or using a Raspberry Pi, the UI should be the same.
- Modern look – We have been using the same UI for quite a while now, and our old theme maintainer had moved on due to lack of time. So we wanted to go with something fresh, new, and modern.
To help us address these items, we tracked down Daniel Ruiz de Alegría and started the development of a new theme running on Xfce. Why Xfce? After reviewing the above issues, we felt that Xfce addressed them best while still being accessible to the majority of users.
The solution we’ve committed to is lightweight and can run on all levels of Kali installs. It is functional in that it handles the various needs of the average user with no changes. It is approachable where it uses standard UI concepts we are all familiar with to ensure there is no learning curve. And it looks great with modern UI elements that make efficient use of screen space.
We are really excited about this UI update, and we think you are going to love it. However, as UI can be a bit like religion, if you don’t want to leave Gnome don’t worry. We still have a Gnome build for you, with a few changes already in place. As time goes by, we will be making changes to all of the desktop environments we release installs to get them “close” to a similar user experience no matter what DE you run. There will be limits to this, as we don’t have the resources to heavily invest in tweaking all these different environments. So if there is something you would like to see, feel free to submit a feature request!
We have also released a FAQ about the new theme that you can find on our docs page. This includes some common items like how to switch to the theme on your existing install, how to change off of it if you don’t like it, and so on.
Kali Undercover
With the change to the environment, we thought we would take a side step and do something fun. Thanks to Robert, who leads our penetration testing team, for suggesting a Kali theme that looks like Windows to the casual view, we have created the Kali Undercover theme.
Say you are working in a public place, hacking away, and you might not want the distinctive Kali dragon for everyone to see and wonder what it is you are doing. So, we made a little script that will change your Kali theme to look like a default Windows installation. That way, you can work a bit more incognito. After you are done and in a more private place, run the script again and you switch back to your Kali theme. Like magic!
Kali-Docs is now on Markdown and new home (/docs/)
This may not be as flashy as the new theme, but the changes to the docs we have done is just as significant.
One of our go-forward goals with Kali is to move more of the development into the public and make it as easy as possible for anyone (that means you!) to get involved and contribute to Kali. That’s what our move to GitLab earlier in the year was all about. Another part of this is changing how we deal with docs.
We have since moved all of our documentation into Markdown in a public Git repository. From here on out anyone, not just Kali staff, can contribute to better documentation through merge requests. We will still approve any content changes, but once merged, changes will be automatically available on the docs section of our website.
We encourage everyone to get involved! If you see something wrong in the existing docs, change it! If you have an idea for new docs, write it! These sorts of contributions make Kali better for everyone.
This is just the first step. With this change in place, coming soon watch for a kali-docs package in Kali that gives you full offline access to the documentation on every install of Kali. Perfect for those situations where you are working in a closed-off environment with no Internet access.
Public Packaging
One of the more significant new documents we have done is documenting how you can make a new package that will get included in Kali.
One of the most common bug reports is requests for us to add new tools or update existing ones. Oftentimes, by the tool developers themselves as they recognize that having their tool in the Kali repo is the easiest distribution channel for security assessment tools there is. The volume of this has always been difficult to keep up with, and we have to make some hard decisions on where to commit our limited resources.
Now with this work-flow in place and documented, you don’t have to wait on us. Go ahead and package up your tool and submit it off to us for approval. This is an awesome way to get involved with improving Kali.
BTRFS during setup
Another significant new addition to the documentation is the use of BTRFS as your root file system. This is an amazing approach documented by Re4son, that when done gives you the ability to do file system rollbacks after upgrades.
When you are in a VM and about to try something new, you will often take a snapshot in case things go wrong you can easily go back to a known-good state. However, when you run Kali bare metal that’s not so easy. So you end up being extra careful, or if things go wrong have a lot of manual clean up to do. With BTRFS, you have this same snapshot capability on a bare metal install!
As this is new, it’s not integrated into our installer yet. Once we get some feedback on how it’s working for everyone, the next step is to streamline this and make it an easier option in our installer. So if you try it out, be sure to let us know how it works for you!
PowerShell
On to other features, in case you missed it PowerShell is now in Kali (We have a blog post about it). This has been really great to bring the ability to execute PowerShell scripts directly on Kali.
Dr fone free full version. NetHunter Kex – Full Kali Desktop on Android phones
Another feature we are super excited about is the introduction of NetHunter Kex. In a nutshell, this allows you to attach your Android device to an HDMI output along with Bluetooth keyboard and mouse and get a full, no compromise, Kali desktop. Yes. From your phone.

We had a live Penetration Testing with Kali course we were teaching, and NetHunter Kex was just in a beta stage. So we wanted to really push the limits. So, in the live course, what we did was attach a USB-C hub to our OnePlus7. This gave us HDMI and Ethernet access. We attached the HDMI to the projector and used a bluetooth keyboard/mouse. With this, we were able to do an entire PWK module from the phone.
This is a feature you have to see to believe. Until you experience it, you won’t fully understand what this provides. With a strong enough phone, this is very similar to using a nice full-featured portable ARM desktop that happens to fit in your pocket. The possible ways you can leverage this in assessments is huge.
To get a full breakdown on how to use NetHunter Kex, check out our docs at.
ARM
2019.4 is the last release that will support 8GB sdcards on ARM. Starting in 2020.1, a 16GB sdcard will be the minimum we support. You will always be able to create your own image that supports smaller cards if you desire.
- RaspberryPi kernel was updated to 4.19.81, and the firmware package was updated to include the eeprom updates for the RaspberryPi 4.
During the release testing, a limited number of devices were not showing the Kali menu properly. This was not critical enough to delay the release, so instead as a work-around you can run the following command to display the menu correctly: apt update && apt dist-upgrade
Once this completes, log out, so you’re back at the login manager. Then switch to a console via CTRL+ALT+F11 (on the Chromebooks this is the key pointing left next to the ESC key).
Login and then run: rm -rf .cache/ .config/ .local/ && sync && reboot
After reboot, the menu will have the correct entries. We’re still looking into why it occurs on only some of the images.
Kali 2019.3 Release Notes
We are pleased to announce that our third release of 2019, Kali Linux 2019.3, is available immediately for download. This release brings our kernel up to version 5.2.9, and includes various new features across the board with NetHunter, ARM and packages (plus the normal bugs fixes and updates).
As promised in our roadmap blog post, there are both user facing and backend updates.
NetHunter Updates
The NetHunter crew has been adding in features left, right, and center to their project. One thing to note is package management is done through the F-Droid compatible NetHunter store, so you can even choose to have a NetHunter device without any Google Play.
The proxmark3 client supports RDV4 out of the box and NetHunter now also works with Android’s new partition layouts (A/B partitions no longer have one boot partition and one recovery partition. They are all the same, but twice! A few paths have also changed, such as /system now actually being under /system/system), which allows it to be built for the latest generation of devices.
Plus, there are new apps in the NetHunter app store, thanks to @mayank_metha for Rucky and the Termux team for Termux.
There are 4 additional images for you to try NetHunter on (some may look familiar, as they are back due to community demand):
- LG V20 International Edition
- Nexus 5X
- Nexus 10
- OnePlus 7 (Our new flagship device!)
With this announcement, the OnePlus 7 is now the phone we recommend for Kali NetHunter. It is the latest and greatest flagship device for half the price of other devices. The specifications are as follows:
- Snapdragon 855
- 8GB RAM
- 256GB storage
- Still cheaper than Google pixel 3a (mid-range phone!) ;)
And here is a sneaky peak at the new boot animation, across all devices:
CloudFlare
Kali Linux is Open Source, and Cloudflare hearts Open Source – so it’s a perfect match! As a result, CloudFlare has graciously allowed us to use their content delivery network (CDN) to mirror our repository, allowing us to now distribute our content through them. A more technical breakdown can be found on their blog.
We are currently running the CloudFlare services side by side with our standard and community mirrors.
If you notice the kali.download domain appearing on screen when you run apt update, this means you’re using CloudFlare’s services.
Kali Status
We now have a status page – status.kali.org. This provides an overview of all public facing domains and allows you to check if they are responding correctly. We have included all the sites we control, as well as the community mirrors for the repositories, allowing you to see everything you could possibly use (even if you are unaware)!
Note: Our load balancer on http.kali.org should automatically detect when a mirror is not responding and redirect you to one that is. As such, apt should always work (even if slow at times).
Metapackages
We already announced the changes to metapackages in a previous blog post, and the Kali tool listing page goes into more detail on it. However, to recap, the default toolset going forward has changed. To help with this transition, for this release only (Kali 2019.3), there is a one-off, extra image called kali-linux-large-2019.3-amd64.iso, that contains all previous default tools.
Going forward, during our release cycle, we will be evaluating which tools belong to each group:
- Kali-linux-default – tools we believe are essential to a penetration tester
- Kali-linux-large – for penetration testers who have a wider set of non standard/common situations
- Kali-linux-everything – for those who want it all (and without Internet access during the assessment)
With the switchover to GitLab (read more here), we will soon begin accepting community package submissions. This means that anyone can directly submit improvements to us–anything from minor fixes and patches to complete tool packages is encouraged. We’re currently working through the documentation on how to create a package, making it easier for folks to get started and help out. More details to come later this year.
We also noticed some packages failed to build on certain ARM architectures, which has now been fixed (allowing for more tools to be used on different platforms!).
/addictive-keys-xln-audio-vst-crack.html. Helper Scripts
There’s a wide range of tools in Kali. Some tools are designed to be used on Linux, some are designed for Windows (and we can still use them with WINE), and some are static resources. During our recent metapackage refresh, we took the time to create a few “helper scripts”.
You may have installed a package, gone ahead and typed in the package name to run it, and the response back was command not found. Not any more!
We understood it may not have been obvious how to use them straight away. As a result, all of our static resources should now be easy to find. Just type in the package name (Such as PayloadsAllTheThings, SecLists, WebShells and Wordlists to a name a few), you’ll see a brief description, a directory listing, and then be moved to the folder.
Tool Updates & New Packages
As always, we have our updates for all our tools, including (but not limited to):
- Burp Suite
- HostAPd-WPE
- Hyperion
- Kismet
- Nmap
There is a new tool (and it is included by default), amass, that has been well received in the bug bounty world.
GNOME Users
If you use the default Kali image, it is (currently) using GNOME for the desktop environment. If you used the command line for a period of time, chances are you noticed it was refreshing the repositories in the background. This has now been disabled.
ARM Update
For ARM devices this release, we have added support for the PINEBOOK as well as the Gateworks Ventana machines.
The RaspberryPi kernel has been bumped to version 4.19.66, which includes support for all of the RAM on 64-bit versions of the RaspberryPi 4. The RaspberryPi Zero W has seen improvements as well.
Bluetooth firmware that was accidentally dropped has been added back in, and the rc.local file has been fixed to properly stop dmesg spam from showing up on the first console.
All of the RaspberryPi images have had their /boot partition increased, which is required due to the size of the new kernel packages.
The ODROID-C2 has been bumped to the 3.16.72 for its kernel.
All images now run dpkg-reconfigure xfonts-base on their first boot – this will cause a bit of a slow down for the first boot, but the result is that if you use VNC to any of them, they will no longer show a blank screen.
On the WSL front, we have added WSL ARM64 support, which you can find in the Windows store today.
Official Kali Linux LXD Container Image Released
LXD is a next generation system container manager. It offers a user experience similar to virtual machines but using Linux containers instead.
It is image based with pre-made images available for a wide number of Linux distributions and we are excited to announce that Kali Linux is now one of them. We are working on the documentation but would like to share the excellent article from Simos Xenitellis in which he details how to install and run Kismet in a LXD Kali container.
Setup Notes
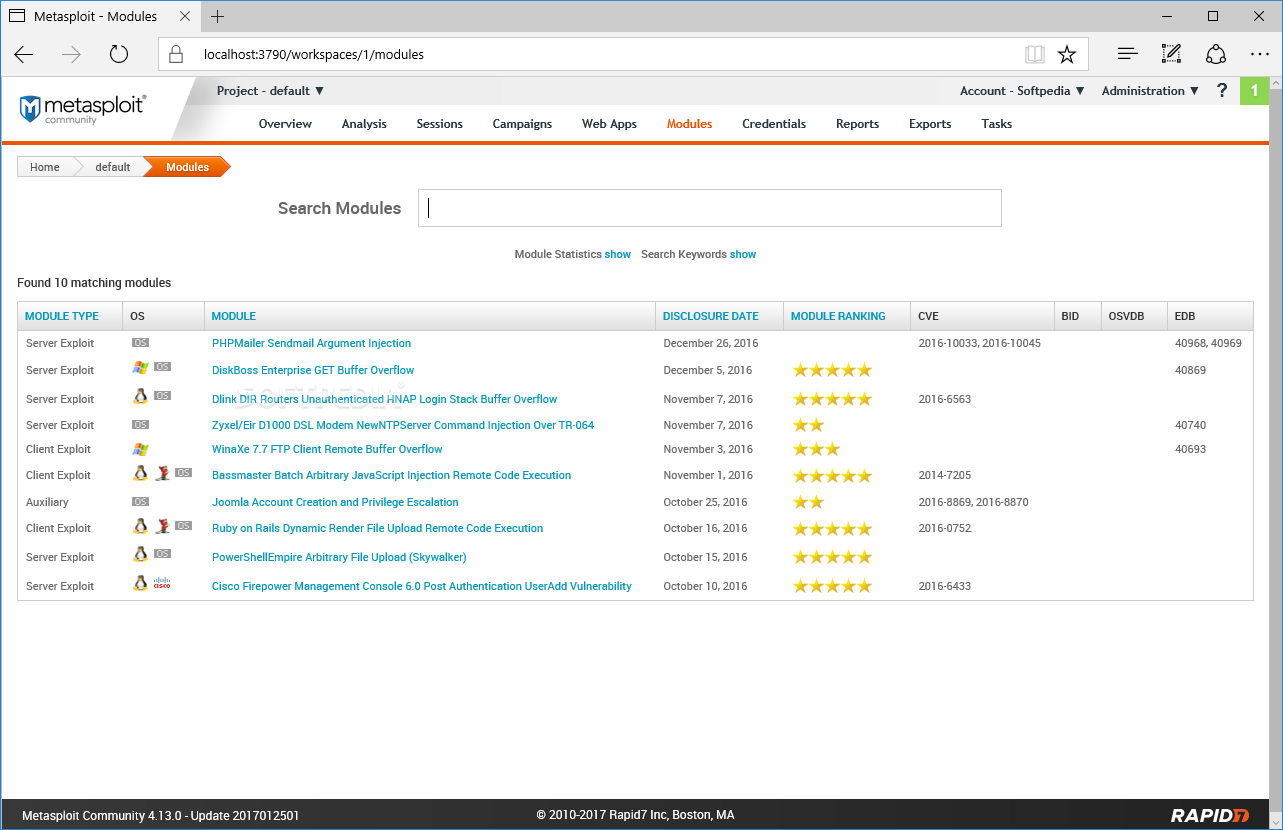
Install Metasploit On Windows 10
A couple of notes when installing Kali. If you choose to install Kali in a VM (rather than downloading our pre-made image), during the setup process, it should now detect if its running in VMware or VirtualBox and install the necessary packages to give you the best experience possible. However, if you have upgraded Kali rather than doing a fresh install, and never got around to installing these packages, the process has been automated by just running kali-setup. This program will have more functionally at a later date.
If you use Kali in a VirtualBox, please ensure you allocate 32 MB or more video memory to the VM, otherwise you may now run into some “interesting” issues where the screen is frozen after login through the graphical greeter, as if the computer had crashed, except that it’s working (you could confirm it by switching to another virtual terminal). If you are affected by this problem, you might see the following message from the kernel: [drm] Error -12 pinnning new fb, out of video mem?.
If you are using Kali Linux via Vagrant, the path has now changed. It can now be found here: kalilinux/rolling.
Download Metasploit Windows 10
Other Downloads:
Download Metasploit 32 Bit Windows
Software similar to Kali Linux 4
Metasploit Pro 32 Bit Download
- 35 votesArch Linux is an independently developed, i686/x86-64 general purpose GNU/Linux distribution versatile enough to suit any role.
- Freeware
- Windows
- 45 votesThe Kali Linux NetHunter project is the first Open Source Android penetration testing platform for Nexus devices, created as a joint effort between the Kali community member “BinkyBear” and Offensive Security.
- Freeware
- Android
- 123 votesDownload the latest version of the Linux operating system.
- Freeware
- Linux